Background
Humphrey Browning, Deep-Secure, discussed “why organisations should move beyond detection” during this month’s SWCSC Networking Meeting. Deep Secure is based in Malvern, UK, founded in 2009. Technologies: Policy and enforcements. Target Markets: Defence, Gov, CNI, Financial Services.
Beyond Detection Report, Gartner.
Deep Secure has come up with an innovative way to stop Malware. Solve the problem with sharing in 21st Century – data can carry malware and attackers exploit the data being carried by infecting it with malware – separate the business data from the malware is the trick to tackle the malware problem in a different an effective way.
Detection based defences: Threat Detection, Isolation, Advanced Threat Detection, Threat Removal (these methods are not as sufficient now that malware is being generated more and is becoming more and more sophisticated – the way attackers work has been developed and changed within the last 4 years. There is still room for attackers to get past anti-malware and anti-virus devices and software – they work out if they are in a sandbox, if the sandbox is running and learnt their environment so remained dormant until they were out of the sandbox.)
Malware: Zero days are being used in a different and more effective way. Steganography are really hard to detect.
The Problem With Weaponised Content:
Zero Trust: Influential organisations are now using this approach to look at malware in a different way.
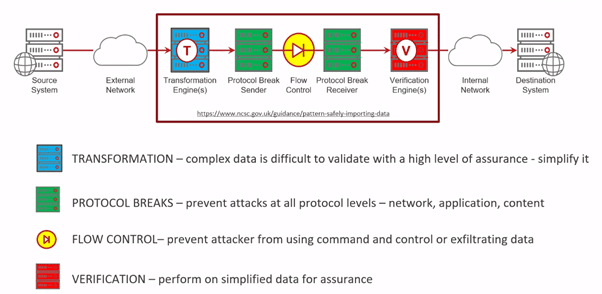
NCSC Secure Data Import Pattern:
The method: Beyond Detection – How to stop malware without looking for it:
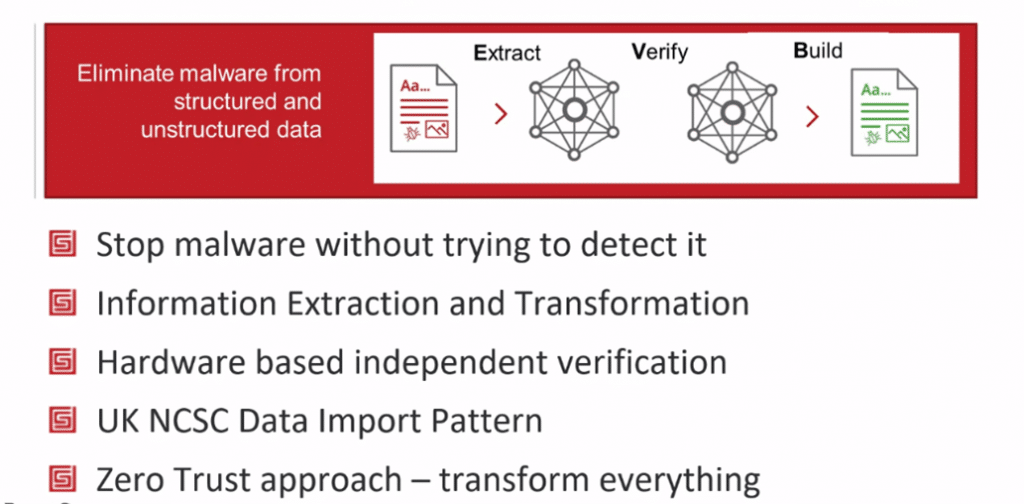
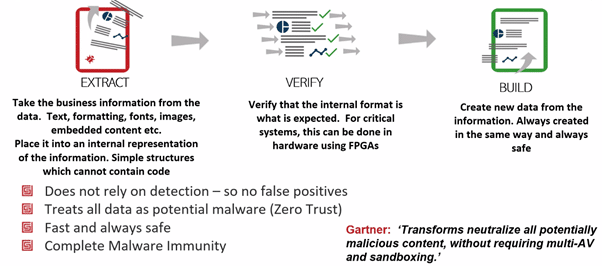
- Deep Secure have looked at a different approach. Defeating threats without actually detecting them – the new way of preventing malware. Set out to build a bran new zero-trust application. Designed to be attacked. Built a 3-stage process to eliminate malware from structured and unstructured data. Not looking for malware – just looking for structures in the data to prevent malware. It is an incredibly effective way to stop malware.
Deep Secure Zero Trust Threat Removal Process – Secure by Design:
FAQ’s
- What about content you cannot transform?
- Encrypted files: Need to decrypt first
- Password Protected files: Need to know the password before getting to the files
- Macros will want to be let in
- File types you do not currently support
- Does threat removal cause delay? Downloading a large file takes as long as performing the Zero Trust Threat Removal and cannot see it running – can work as normal as it runs in the background
- What about new threats? Do not allow new features and new threats in – protected from these
Threat Removal Use Cases:
-
- Secure File Transfer
- Secure Email
- Web Services
- Secure Web Browsing
- Isolated Web Browsing