In November, we had the opportunity to learn more about Principles Based Assurance led by the NCSC’s Head of Technical Assurance Group (TAG), Helen Lovekin. Cybersecurity is integrated into the fabric of our livelihood; extending from energy and transport, to banking and communications. Our reliance on this technology leaves us vulnerable if it were to go wrong, hence the need to boost our trust in these ever-evolving systems.
What is Technology Assurance?- A Statement of Confidence
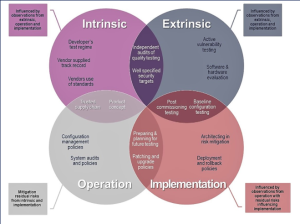
Lovekin describes technology assurance as the level of confidence in which we believe a technology or system can keep itself and its protected individuals safe from external threats it is likely to encounter. It is also a way to evaluate your business’ cybersecurity needs and apply appropriate actions to mitigate the risk of threat. Since the publication of the Orange Book in 1985 we have seen decadal progress in threat mitigation, leading to the Commercial Product Assurance between 2014 and 2019. While, technology has progressed at a far more rapid rate. Below we can see that the different approaches can be broken down in to 4 sections:
Weird Outcomes of Product Assurance Schemes
- Evaluated products have immediate legacy technical debt.
- Parts of a product don’t get tested, so vulnerabilities can exist from Day One.
- Security doesn’t work for people.
- Only certain ‘shaped’ products pass.
- Consumers choose old products with badges rather than new ones without.
- Vendors have to pay huge amounts of money for little ROI.
- Vendors set their own homework.
- The “race to the bottom” – vendors choose the ‘easiest’ lab, labs try and make it easier.
- Security is only focused on products, not the systems they’re going into.
- Only gaining assurance in security products, not technologies that need to be secure.
- Focus is on the technology, not how the technology is being used.
- Evaluation is at a point in time, not when the technology is going to be used.
- Sometimes, assurance can be based on a ‘pinky promise’.
Transforming the Way We Provide Technology Assurance
By changing our approach we will be able to:
-
- Drive innovation & facilitate diversity in technology
- Enable flexibility & agility
- Support UK industry and prosperity
- Facilitate better risk outcomes
- Have impact at scale
- Common and accessible language
- Improve security engineering of technologies
While supporting a vast variety of consumers and empowering them in their decision when selecting cybersecurity protection systems and technologies, that are appropriate to them. You can read more this in the White Paper which sets the guidelines of how the process will be implemented step by step from the NCSC.
[foogallery id=”997″]
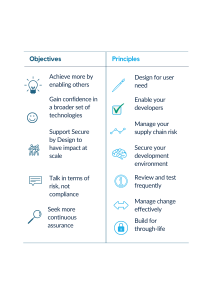
Objectives Guided by Principles
The objectives of the project are guided by a set of seven principles that help to increase the resilience and effectivity of technologies when encountered with cyber attacks. When designing these systems the NCSC will use the combination of the desired outcomes and the principles to assess the suitability of the product and competence of the product developer and determine the outcome of the resultant product. It is vital that a secure product is made. The NCSC says that you need to be protected against:
-
- unauthorised access
- data transfer
- data modification (internal and external sources)
This applies even if you are in the development stage. Maintaining confidentiality and integrity from the creation of test plans and source code to requirements and documentation. This helps to ensure that the system is not exploited by any vulnerabilities, both malicious and accidental, developed at any stage of the project.
If you have enjoyed this and want to discover more we highly recommend visiting Helen Lovekin and Deputy Director of Cyber Skills and Growth at NCSC Chris Ensor’s, blog posts that further detail the future of technology assurance and the principles that guide this development.